It was discovered a site containing a complete full
infrastructure for preparing phishings attacks. In this criminal site has been
found all kind of malicious scripts, phishings kits, exploits & spam tools
necessary to carry out fraudulent activities to steal credentials and obtain
confidential user data from bank financial institutions in Europe, mainly in
Spain, UK and Italy.
With all this amount of malicious material is possible
to do a complete fraud lifecycle.
About traces and comments in malicious scripts it
seems that this infrastructure belongs to Romanian criminal groups.
The workflow of criminals takes place in three stages
A first step in locating legitimate Internet servers that have installed Phpmyadmin database management application, and have installed phpMyAdmin versions 3.3.10.2 y 3.4.3.1 vulnerable to certain exploits designed by criminals to upload malicious code to that legitimate server.
To find that phpmyadmin vulnerable servers, the
exploit script send requests on Bing searcher to find web addresses that
contain in its URL the following directory paths:
These malicious scripts exploit a weakness in the
server configuration options of phpmyadmin application to upload a phpshell
that allows criminals to take full control of hacked machine.
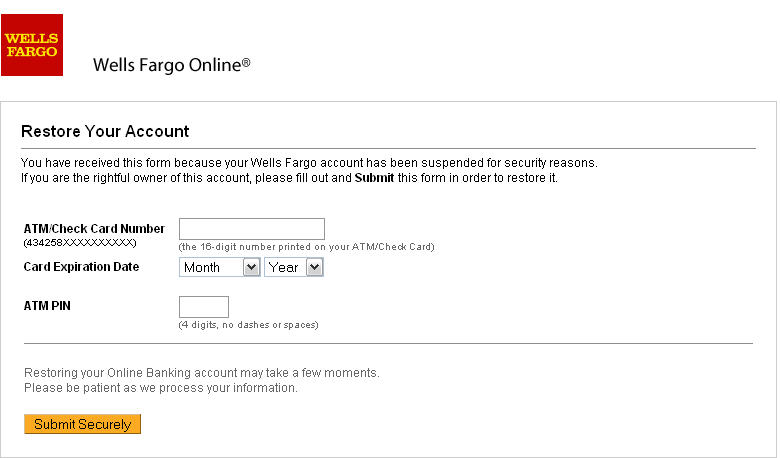
The next stage is basically the preparing the phishing
of target banks. Criminals use the phpshell uploaded previously in compromised
server to upload the phishing kit. This kit usually consists a compressed file
type .Zip containing the exact clone copy of the financial institution against criminals
want to perform the phishing attack.
The main purpose of these phishings is to obtain
confidential data from credit card of costumers pretending to be legitimate
bank requests to the client.
For this cause phishings simulate legitimate pages of
the bank, but criminals are not interested in doing electronic banking fraud
operations. They use phishings to obtain supplement data from the credit cards
of customers and especially to get the ATM PIN code of credit card. This ATM
PIN code is used to hire and activate financial services against the crefit
card that will be used by criminals for fraudulent business transactions or to
be used in electronic commerce.
The last stage of the fraud will be to launch a massive
spam campaign with emails containing that fake URLs where are hosted phishings
to try to trick users to visit that fraudulent addresses and claiming to complete their confidential bank details.
The SPAM tools and mail address lists for spamming are
also hosted on the criminal located server:











No hay comentarios:
Publicar un comentario
Nota: solo los miembros de este blog pueden publicar comentarios.