It has been found a new Control Panel focus to query and extract data from repositories of banker Troyans Zeus family and its variants. Like a data mining application is able to connect to different databases repositories that store data stolen by Troyans and search required data using regular expressions.
Access to the Control Panel shows the next information.
This method provides the advantage to criminals of being directly connected to remote databases that contain confidential information from compromised users without having to access the Control Panels where hosted data repositories are. Queries are performed directly on the databases without having to interfere at any time with the operation of the control panel that manages all botnets or zombie machines.
Of this way criminals also avoid leaving traces in web servers every time they have to perform some operation on the captured data leaving no traces in the log files of the web server.
Connection to the databases from Troyan Control Panel is quite simple.
In the Control Panel settings is configure the connection strings of database where the troyan’s repository is stored and Troyan class which wants to extract the information to analysis and process.
Troyan clasees with the application works are: Carbep, Citadel, Ice9, SpyEye, Zeus 1.1 Zeus 1.2 & Zeus2.
All these Troyans are different in their performance but retain many similarities in the manner in which the stolen information is stored in its databases and this Control Panel tools able to adapt to the structure of each Troyan database.
The data search engine in repositories is based on the powerful capacity of regular expressions, This seach engine is visible at next screen.
In this example created by default in the control panel, you can see the regular expression that should be used to locate at Troyan data repository all stolen access credentials that comply the defined format "user/ password" for accessing the legitimate websites of Paypal and Ebay
These regular expressions allow to search at full Troyan database robbed data users by defining variables names of stored passwords or any data that wish to find
With regular expressions is possible to define any text searchable format, such as email addresses, dates, passport numbers, social security numbers, etc. The possibilities are endless.
Is possible even to create search templates and store it for future actions.
The search engine also allows multiples search options, like searching by zombie machines IDs, URLs and even post data captured by users mails headers.
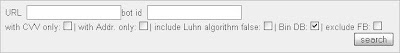
There is even an automated module for searching confidential information of credit cards, in this module you can specify search key fields as the CVV code of the credit card or using the Luhn algorithm.
The Luhn algorithm or "algorithm module 10" is a formula checksum used to validate the identification numbers of credit cards.
Suscribirse a:
Enviar comentarios (Atom)





No hay comentarios:
Publicar un comentario
Nota: solo los miembros de este blog pueden publicar comentarios.